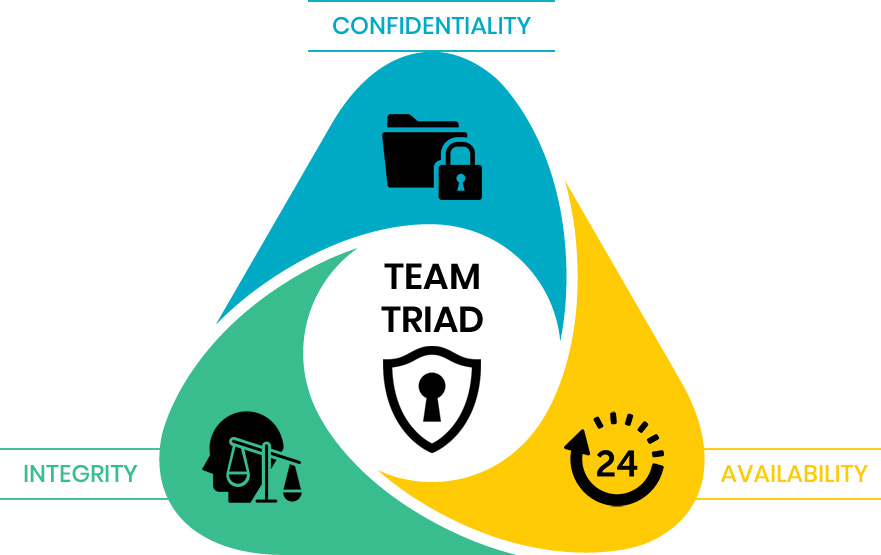
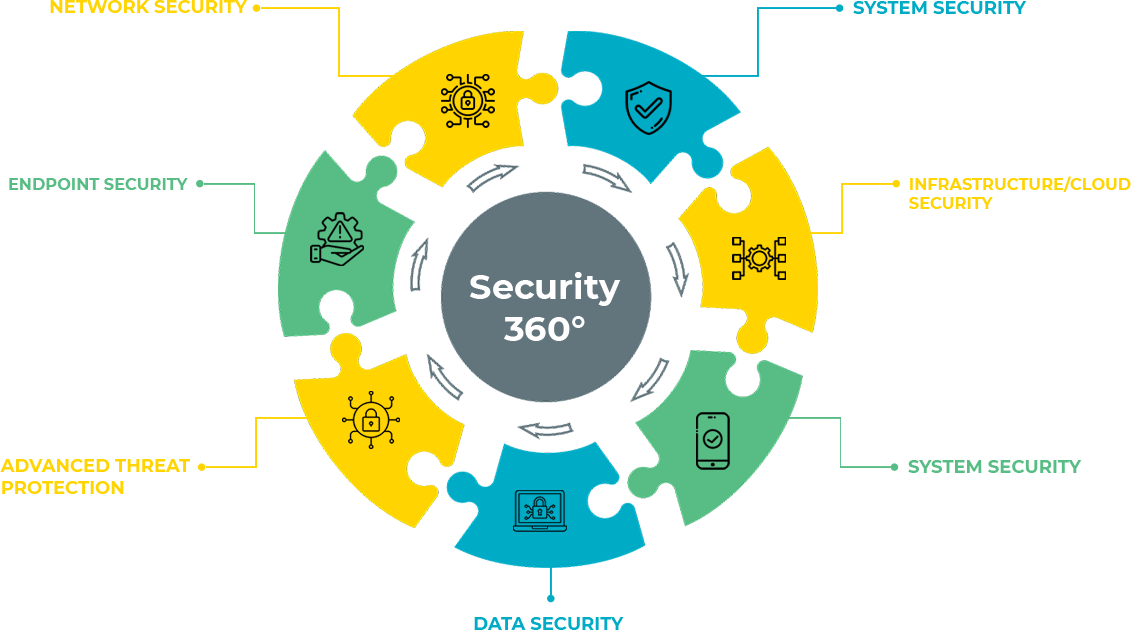

Global Standards, Working with Leading OEM's, Solution Based Approach - 50+ clients

Deep knowledge, across industry.

Dedicated Team of Sales Specialist, Pre Sales Specialist, solution architects, delivery team and diverse set of OEM's.

Work collaboratively for implementation and distribution of products and solutions across sectors.

Xanadu, where the magic happens. come and feel the technology. experience in Live environment.
Talk to our
Cyber Security Expert

























Visit our page at Team Computers
Send us your CV showcasing the best of your skills at careers@teamcomputers.com
Interested In Details? Visit: Work|Team Computers